Category:Information security
Jump to navigation
Jump to search
| To display all parents click on the "▶": |
protecting information by mitigating information risks | |||||
| Upload media | |||||
| Instance of |
| ||||
|---|---|---|---|---|---|
| Subclass of | |||||
| Part of |
| ||||
| Facet of |
| ||||
| |||||
Subcategories
This category has the following 24 subcategories, out of 24 total.
Media in category "Information security"
The following 110 files are in this category, out of 110 total.
-
"Confidential" coversheet (6323055606).jpg 1,944 × 2,592; 2 MB
-
"Restricted Data" stamp (6322624283).jpg 2,592 × 1,944; 1.67 MB
-
"Secret-Restricted Data" cover sheet (6322546385).jpg 1,944 × 2,592; 1.63 MB
-
1 частина.jpg 960 × 720; 124 KB
-
2008 Taichung IT Month Day2 III Pavilion Information Security Area.jpg 1,728 × 2,304; 1.09 MB
-
2008 Taipei IT Month Day8 III Information Security Pavilion.jpg 2,304 × 1,728; 1.57 MB
-
2010-T10-ArchitectureDiagram.png 947 × 360; 110 KB
-
A Reference Model of Information Assurance and Security (RMIAS).png 3,531 × 3,436; 2.28 MB
-
AEC Top Secret Cover Sheet (6520387149).jpg 800 × 1,056; 403 KB
-
ARP attack illustration.png 383 × 368; 14 KB
-
Boletim de Urna.jpg 900 × 1,600; 90 KB
-
BufferOverFlow.JPG 611 × 554; 33 KB
-
C-I-A diagram-ru.svg 512 × 512; 2 KB
-
Card 112 codes.png 2,048 × 1,312; 382 KB
-
Chain of trust ru.svg 645 × 386; 51 KB
-
Chain of trust.svg 645 × 379; 56 KB
-
Chiffrement des données depuis un systeme bluetooth.jpg 960 × 720; 39 KB
-
Chntpw.png 754 × 335; 426 KB
-
Chntpwinitvbox20230911.png 720 × 400; 5 KB
-
Chunk.png 801 × 127; 5 KB
-
CIAJMK1209-ar.svg 496 × 496; 250 KB
-
CIAJMK1209-en.svg 496 × 496; 177 KB
-
CIAJMK1209.png 1,216 × 1,193; 540 KB
-
Clé d'initialisation.jpg 1,280 × 960; 30 KB
-
Computer-lock.gif 48 × 48; 6 KB
-
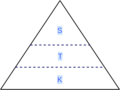
Confidentiality Integrity Availability triangle.png 416 × 350; 31 KB
-
Confidentialité-Intégrité-Disponibilité.png 366 × 316; 34 KB
-
Defense In Depth - Onion Model -kn.svg 500 × 500; 8 KB
-
Defense In Depth - Onion Model ml.svg 533 × 533; 7 KB
-
Defense In Depth - Onion Model-ar.svg 500 × 500; 670 bytes
-
Defense In Depth - Onion Model-gu.svg 500 × 500; 7 KB
-
Defense In Depth - Onion Model-mr.svg 500 × 500; 7 KB
-
Defense In Depth - Onion Model-pa.svg 500 × 500; 7 KB
-
Defense In Depth - Onion Model-te.svg 500 × 500; 4 KB
-
Defense In Depth - Onion Model.svg 500 × 500; 658 bytes
-
Demilitarized Zone Diagram.png 669 × 415; 58 KB
-
Demyo, Inc.jpg 320 × 180; 10 KB
-
DLP Veille Techno.jpg 791 × 381; 34 KB
-
Equifax-Report-Dec2018.pdf 1,275 × 1,650, 96 pages; 2.43 MB
-
Exemple Meta Modèle Taguchi.png 809 × 464; 120 KB
-
Fig-IAM-phases.png 806 × 506; 68 KB
-
Fixation de session.png 952 × 612; 93 KB
-
Future of mobile security.pdf 1,239 × 1,754, 12 pages; 110 KB
-
Government Security Classifications Policy.png 1,000 × 400; 17 KB
-
Hall Of Fame Adobe 2014.jpg 2,400 × 2,400; 336 KB
-
Haroon meer keynote speaker at nullcon 2018.jpg 2,411 × 839; 308 KB
-
HeapBlock.png 526 × 235; 3 KB
-
IDsec.svg 971 × 737; 443 KB
-
Information Security Incidents by Category, Fiscal Year 2014.svg 675 × 394; 316 KB
-
Information Security Promotional Area, Taipei IT Month 20171209.jpg 4,400 × 3,300; 1.78 MB
-
InfoSec at Olympia London, April 2006.jpg 1,632 × 1,224; 387 KB
-
IntergrationCCdansProjet.png 531 × 437; 129 KB
-
IntégrationCCdansProjet.jpg 531 × 437; 35 KB
-
Isms framework.jpg 600 × 411; 67 KB
-
ISO27003.png 939 × 330; 101 KB
-
ISO27004.png 1,004 × 749; 140 KB
-
ISO81001-1 ED2-FIG1-A.ai.svg 794 × 794; 22 KB
-
Jaya Baloo at Blackphone Launch.jpg 5,976 × 3,992; 6.3 MB
-
La huella digital.jpg 443 × 296; 12 KB
-
Meta Modèle Taguchi.jpg 809 × 464; 37 KB
-
Mind map of information security.svg 3,080 × 6,470; 185 KB
-
Modello di Gordon-Loeb.png 831 × 531; 52 KB
-
Morrisworm.png 763 × 385; 11 KB
-
Multivoto.png 800 × 1,404; 240 KB
-
Nmap-behind-31c3.png 1,343 × 627; 122 KB
-
Octave like.jpg 350 × 254; 16 KB
-
Office of the JSC State Technical Service.png 1,920 × 672; 2.02 MB
-
OSSTMM3 Framework.png 785 × 733; 80 KB
-
Padlock with lattice background.png 910 × 910; 660 KB
-
Philippe Langlois at hack.lu 2010.jpg 5,616 × 3,744; 5.16 MB
-
PortadaSeguridadinformática.png 800 × 600; 658 KB
-
Positive Hack Days 2011 год.jpg 800 × 566; 135 KB
-
Replay attack on hash.svg 1,052 × 744; 27 KB
-
Scadasl.png 355 × 355; 139 KB
-
Secure Coding for MediaWiki Developers.pdf 2,133 × 1,600, 30 pages; 145 KB
-
Sensitive-electronic-devices.jpg 424 × 244; 52 KB
-
Shredding Console.jpg 4,000 × 3,000; 3.25 MB
-
Stk-turvalisus.png 323 × 243; 3 KB
-
Taback Coupland.png 1,050 × 450; 41 KB
-
Tekbin cassonetto per la distruzione certificata documenti.jpg 1,241 × 1,754; 515 KB
-
Tetiana Dmitrivna 3.png 1,422 × 800; 708 KB
-
Tetyana Dmitrivna 2.png 1,422 × 800; 721 KB
-
The Risk Management Process.png 696 × 589; 274 KB
-
US classification colors.svg 168 × 230; 598 bytes
-
USB Flash Memory Drive SanDisk cruizer profile.JPG 1,032 × 1,344; 209 KB
-
VERTRAULICH.jpg 1,340 × 1,823; 1.73 MB
-
Visual crypto animation demo.gif 339 × 100; 83 KB
-
Volker Lüdemann photographed by Aileen Rogge.jpg 5,315 × 3,543; 6.06 MB
-
WAF Archi.png 897 × 267; 64 KB
-
WikiPress 7 Computersicherheit.pdf 743 × 1,120, 179 pages; 6.84 MB
-
Willis-robert-hacker (cropped) (cropped).jpg 203 × 270; 11 KB
-
Willis-robert-hacker (cropped).jpg 307 × 409; 23 KB
-
Willis-robert-hacker.jpg 800 × 1,086; 123 KB
-
Алексей Андреев на PHDays 2012.jpg 800 × 533; 95 KB
-
Архитектура Membership API.png 511 × 567; 76 KB
-
Брокер сетевых пакетов.png 6,073 × 2,953; 581 KB
-
Диаграмма5.JPG 530 × 532; 80 KB
-
Загроза інформаційної безпеки.png 2,604 × 1,082; 419 KB
-
КАРТА ЗНАНЬ штучні загрози.jpg 2,284 × 908; 128 KB
-
КартаЗнаній Узун Ксенія 30,04.2020.jpg 2,066 × 812; 109 KB
-
Конкурсный макет железной дороги.jpg 800 × 533; 227 KB
-
Курцевич Ольга New-Mind-Map.jpg 1,866 × 1,052; 119 KB
-
Посетители PHDays 2011.jpeg 864 × 701; 245 KB
-
Прохождение лазерного поля полосы препятствий.jpg 800 × 533; 134 KB
-
Цикл Деминга для СОИБ.JPG 730 × 478; 72 KB
-
Частина 2.jpg 960 × 720; 92 KB
-
شعار بروكن سايفر.png 1,010 × 1,066; 133 KB
-
قائمه شرف شركه سوني.jpg 625 × 375; 27 KB